A recent Accenture ‘State of Cyber Resilience’ report researched the differences between Leaders and Non-Leaders in cyber security, with 17% of their 4,644 respondents falling into the leader definition and the remaining 83% defined as non-leaders.
Why does this research matter to B2B telecoms service providers? Well the demographics of this research focused on global organisations with revenues of more than $1 billion. These are the ~1% of organisations that account for over 76% of worldwide revenue.
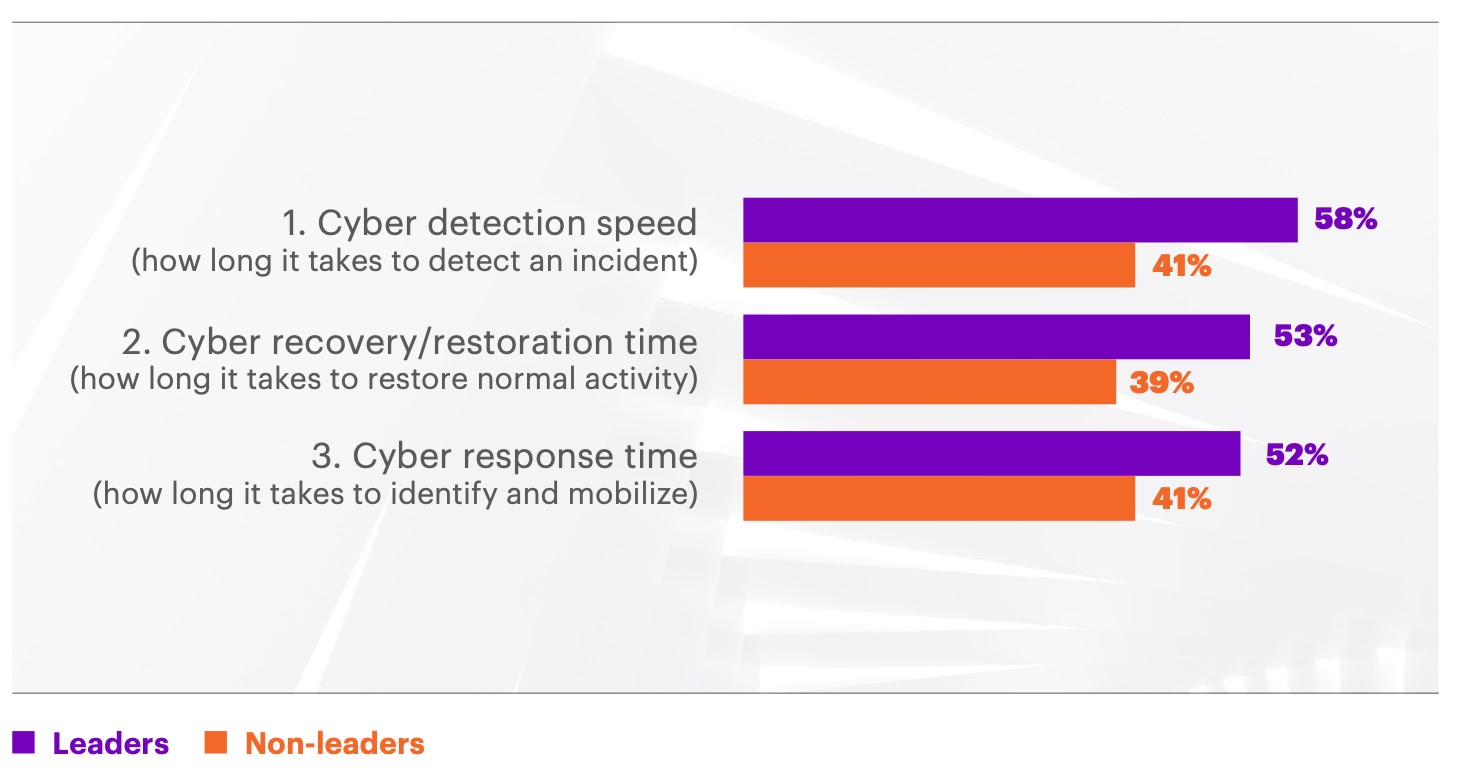
I would be shocked if 83% of these global companies are still failing to recognise the dramatic impact that cyber-attacks can have on their businesses, employees, partners and consumers. The 17% of leaders will have the budget, resources and capability (technology and skills) available to address cyber attacks. But this doesn’t mean they are immune to being attacked. In fact, being a leader just means they’re 4x faster at stopping attacks and finding breaches faster, 3x better at fixing breaches and 2x better at reducing breach impact. So, they’re still being attacked, but are more efficient at dealing with the situation.
The 83% of non-leaders are characterised as being 4x slower at stopping attacks, 3x slower at fixing breaches and 2x worse at reducing the impact than the leaders of cyber resilience. That means that attackers can penetrate their business 3x more often, 78% of breaches take longer than a day to detect, 64% of breaches take more than 2 weeks to fix and 76% of breaches have a measurable impact on their business.
As with all research the questions that are asked of respondents go a long way to defining the data provided. Cyber resilience should span everything from the front door (access) to its foundations (program code) and everything in between. Why did none of the respondents list the access (identity and authentication) and program code (security hardening ) as areas that are not included when reviewing what the focus of cybersecurity performance is from the organisations?
Speed of detection, recovery and response is key when combatting cyber-attacks, but it’s also important to understand whether an organisation’s approach to cyber resilience is proactive, reactive or prescriptive.
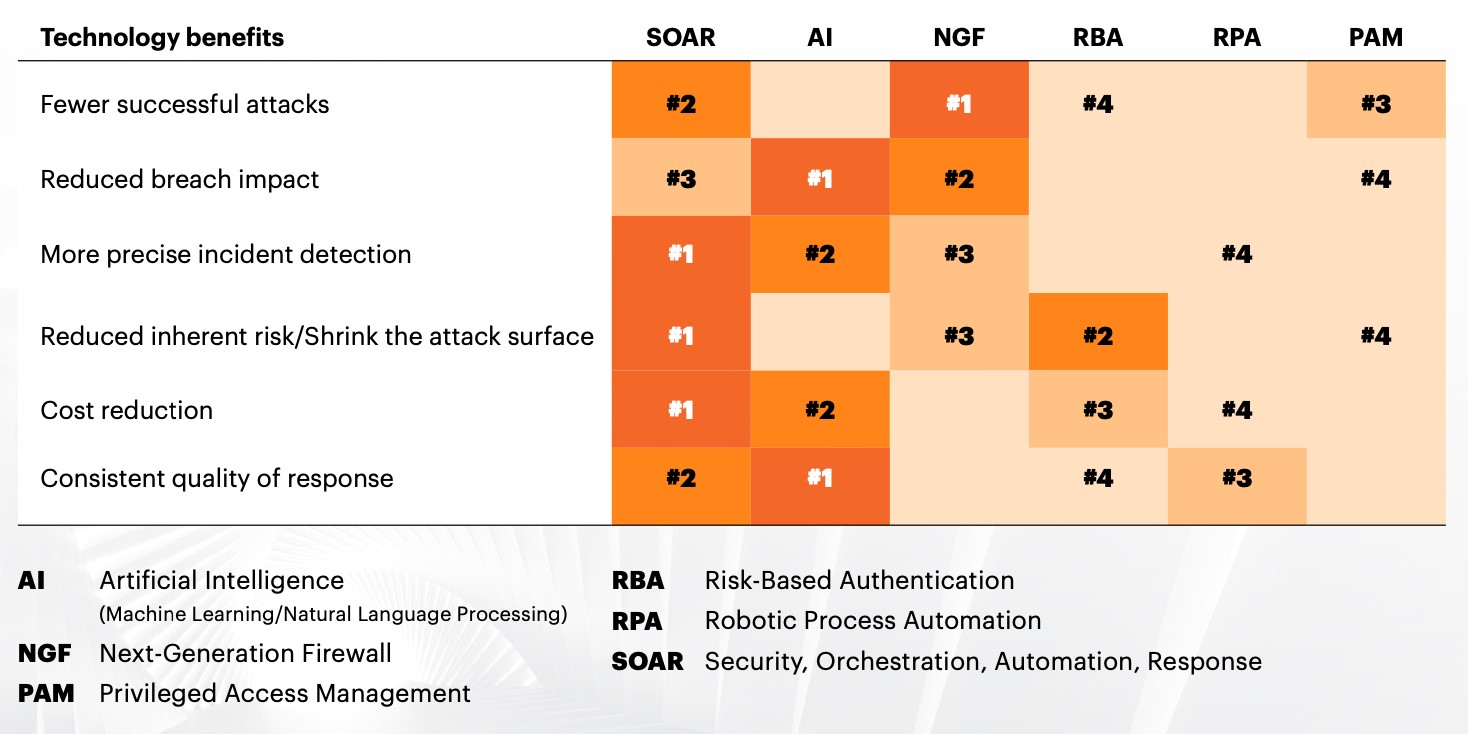
For example:
- Detection: How long it takes to detect an incident is reactive. Whether I have the visibility to identify if we are being targeted is pro-active and what could be targeted and how I’m at risk is prescriptive.
- Recovery: Do I have the adequate recovery capability to respond to an attack is reactive; I have had my core systems tested for BC/DR in case of an attack is pro-active; are there moving ‘air-gaps’ in my supply chain that could be targeted and should be aligned and prepared in case of an attack is prescriptive.
- Response: Do I have the capability to identify and respond to an attack is reactive; what cyber resilience do I have in place across my operating environment to stop, identify and respond to an attack is proactive; are there new attack scenarios that I need to factor into my resilience so attackers see me as difficult to target is prescriptive.
The research by Accenture provides a very good view of how large enterprises are challenging the evolving threat of cyber-attacks. These types of cyber resilience approaches are good for all organisations – immaterial of size – to look at and take away those aspects that apply to their environments and budgets.
The cyber security market is made up of hundreds of different vendor offerings. Sometimes it’s hard to see the wood for the trees, and in such a complex operating environment it’s always easier to think about complexity over simplicity.
The research highlights a key take-away that everyone should take on board. Perform better at the basics and approach the basics from a data-centric security perspective. Every day we read about the latest data breach where thousands and potentially millions of records have been stolen. Each of those records represents an individual, who quite rightly is only interested if you’ve lost their data and what the impact will be on them.
My take on this is that every attack requires access to a system to find the targeted data. In the majority of cases this is via an individual (citizen, customer, employee, stakeholder, etc), providing the access intentionally (known as an insider attack) or innocently.
Going back to basics should prioritise the access protocols given or provided to those individuals. If you evolve your identity and authentication technology and adopt policies that no longer require single or dual passwords/codes and also minimise the interaction that the individual has to provide, by embracing dynamic multi-factor authentication, any personal attribute used to provide access would minimise and mitigate these regular attacks we see every day.
The necessity to security harden the entry point that cyber criminals use to start their attacks would not only protect personal data, but also have a cascading effect – such as reducing the number of phishing attacks (as they no longer have the data to start them) and eliminating SIM-Swap attacks, as you no longer use one-time passcodes to validate users.
Omnisperience’s advice to B2B telecoms service providers
B2B telecoms service providers need to take a close look at the entry and exit points of their systems, both those that are part of the consumer portals used to register, buy and interact, as well as their own internal systems, and re-assess the validity of basic password and two-factor authentication systems that still rely on outdated authentication methods.
In addition they should also be looking to isolate their web portals and internet sites, and review technologies such a web isolation products that mitigate their users from engaging with hidden malware, rogue payment sites and cloned websites.
By adopting what Omnisperience terms a ‘User Isolation Protection’ approach, B2B service providers can ensure they are prioritising the protection of their customers’ and employees’ personal and financial data. (See Omnisperience Green Paper User Isolation Protection)


