Our world is roughly divided into three types of people:
- those that view sharing personal data as an invasion of privacy, believing that ‘Big Brother’ will use this for (presumed) illegal surveillance and data aggregating for purposes not originally intended
- those that accept that their personal data provides value to them by allowing them to engage in business and social activities, widening their view of the world, and accumulating more knowledge and friends
- cybersecurity criminals who see data as their route to success.
Whichever group you belong to, what’s certain is that our lives are increasingly driven by personal data located in multiple repositories across multiple locations.
The UK’s National Cyber Security Centre (NCSC) – the visible arm of GCHQ – which is part of the anglophone intelligence alliance Five Eyes, has highlighted that individuals don’t appear to appreciate the gravity of this situation and the woeful lack of strong online security. In a study it conducted in 2019, over 89% of respondents said they used the internet for online purchases and 42% believed they would lose money from online fraud. Only 15% were confident they could protect themselves from harmful activity.
Not only does this reveal widespread concern amongst digital natives, but extrapolating the findings of NCSC’s survey to the ~4.5 billion worldwide internet connected individuals shows the huge scale of the problem.
But herein lies the problem.
Organisations are bound by regulations such as GDPR that are designed to ensure protection of personal data. We all expect that organisations that hold data will keep it safe and evolve the methods they use for doing so.
However, in the majority of cases, cyber criminals use individuals as access points to exact their attacks – either accumulating data or using the data they’ve already gained to plan their attacks.
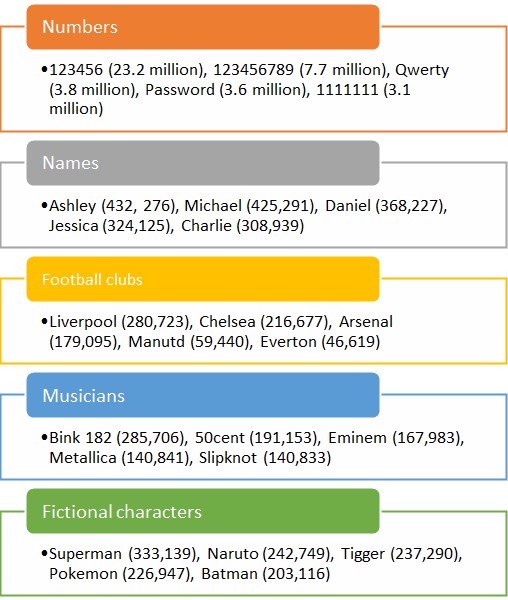
The NCSC found that 70% of these individuals rely on PINs and passwords to secure their devices, trusting similar passcodes for all their activities.
Top 5 passwords used by individuals
Humans will always be the weakest link. And yet they will remain sensitive to how onerous security measures are – never having enough time to spend accessing a platform because they want to spend all the time they do have using it.
While the credentials that individuals use to legitimately gain access to various business and social platforms need to be strong, and users need to ensure that only they (or authorised individuals) can gain the appropriate access and authority, businesses need to help individuals help themselves.
This is why, in order to combat the threats individuals face, as well as the growth in sophisticated attacks, businesses need to change the way they allow access and authority to individuals’ chosen platforms. Businesses should stop relying on password systems or two-factor authentication based on sending the validation code/pins/tokens to the same device that the individual is attempting to gain access from.
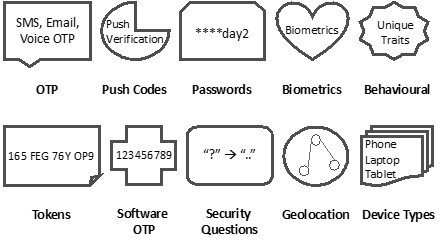
Businesses should instead increase their use of ‘Diverse Multi-factor Authentication’, where the consumable combination of passwords, tokens, codes, pins, biometric, unique content, behavioural, geolocation and device complexity is used with the minimum of user interactions to minimise attitude bias and reduce the ‘air-gap’ between intent and access that cyber criminals exploit.
The capabilities to protect individuals and employees (and associated businesses) can cover the device, authentication and permissions (privileges) either singularly or in combination. What’s important is the capability to protect the individual from themselves, and to minimise the attack surface for cyber criminals to exploit.